Easy solutions and ideas found after long googling or hard coding
If you are minifying scripts and css files using a caching plugin or using FastCGI cache then you might need to warmup your blog after purging your cache. This is a simple warm up cli script for WordPress to initiate cache or HHVM HHBC and making sure all pages/posts do not have errors. Additionally the script creates a urllist.txt file that you can use with siege to test load your server.
//in api/models/User.js
function validationError(invalidAttributes, status, message) {
var WLValidationError = require('../../node_modules/sails/node_modules/waterline/lib/waterline/error/WLValidationError.js');
return new WLValidationError({
invalidAttributes: invalidAttributes,
status: status,
message: message
}
);
}
var User = {
attributes: {
//...
},
ownValidate:: function (values, update, cb) {
//example of not allowed param on update
//if it is an update then do not allow email param
if (update && values.email) {
return cb(validationError({
email: [
{
message: 'Email is not allowed for updates.'
}
]
}, 400 /*status*/));
}
sails.models['user'].findOne(values.email).exec(function (err, user) {
if (err) return cb(err);
if (user) {
return cb(validationError({
email: [
{
value: values.email,
rule: 'E_UNIQUE'
/* unique validation message is left for the default one here */
}
]
}, 409));
}
});
},
beforeCreate: function (values, cb) {
return sails.models['user'].ownValidate(values, false, cb);
},
beforeUpdate: function (values, cb) {
return sails.models['user'].ownValidate(values, true, cb);
}
}
For blueprint custom messages validation
Sitemap Creator is a PHP class which creates XML sitemaps files compatible with the standard sitemaps.org protocol supported by Google and Bing.
Features
- Uses PHPCrawl class to crawl/spider the website and creates URLs set while all PHPCrawl methods and options are accessible through class.
- Ability to calculate Priority, Frequency and Last-Modified date with variety of options.
- Creates sitemaps in gzip format or uncompressed XML.
- Pings search engines with sitemaps locations.
- Reads from CSV files and exports entries in CSV format.
The script creates separate directory for every database and bz2 files for every table inside that database.
#!/bin/sh
#edit these
USER=""
PASSWORD=""
MYSQLDIR="/path/to/backupdir"
MYSQLDUMP="/usr/bin/mysqldump"
MYSQL="/usr/bin/mysql"
echo - Dumping DB structure "$MYSQLDIR"/all.bz2
$MYSQLDUMP --user=$USER --password=$PASSWORD -d --all-databases | bzip2 > "$MYSQLDIR"/all.bz2
echo - Dumping tables for each DB
databases=`$MYSQL --user=$USER --password=$PASSWORD -e "SHOW DATABASES;" | grep -Ev "(Database|information_schema)"`
for db in $databases; do
echo - Creating "$db" DB
mkdir $MYSQLDIR/$db
chmod -R 777 $MYSQLDIR/$db
for tb in `$MYSQL --user=$USER --password=$PASSWORD -N -B -e "use $db ;show tables"`
do
echo -- Creating table $tb
$MYSQLDUMP --opt --delayed-insert --insert-ignore --user=$USER --password=$PASSWORD $db $tb | bzip2 -c > $MYSQLDIR/$db/$tb.sql.bz2
done
echo
done
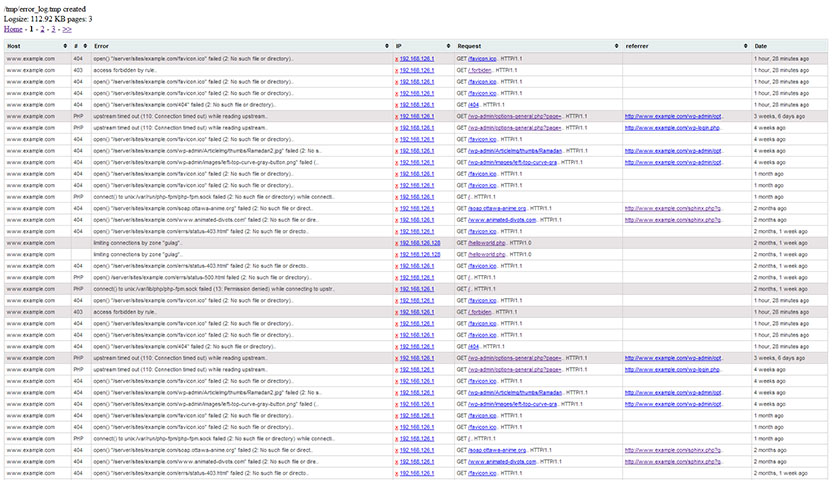 Nginx Error Log Reader is a php reader/parser/analyzer for Nginx error log file. the script is able to read error logs recursively then display them in a user friendly table. Script configuration includes the number of bytes to read per page and allow pagination through the error log . Additionally, table columns are sortable and full description of every error is displayed using MonnaTip.
Nginx Error Log Reader is a php reader/parser/analyzer for Nginx error log file. the script is able to read error logs recursively then display them in a user friendly table. Script configuration includes the number of bytes to read per page and allow pagination through the error log . Additionally, table columns are sortable and full description of every error is displayed using MonnaTip.
For banning Ips, please refer to this post Using iptables to block ips that spam or attack your server