Service Discovery is a simple PHP command to collect and store AWS information such as EC2s and RDSs in the current region and save them with their credentials into an encrypted JSON file on S3. The script later notifies each service via SSH and executes the service discovery client on each instance. Each client downloads the JSON file and uses it to configure different applications. It can easily be automated through Rundeck or Jenkins to be executed after each deploy.
Service Discovery is part of AWS PHP Commands.
Usage:
> php console.php aws:services:discover -h
Usage:
aws:services:discover [options]
Options:
-f, --forceNotify[=FORCENOTIFY] Force Notify [default: false]
-e, --notifyOnly[=NOTIFYONLY] Notify only one of dev,prod [default: false]
-c, --continueOnError[=CONTINUEONERROR] Continue to next EC2 on client failure [default: false]
-h, --help Display this help message
-q, --quiet Do not output any message
-V, --version Display this application version
--ansi Force ANSI output
--no-ansi Disable ANSI output
-n, --no-interaction Do not ask any interactive question
-v|vv|vvv, --verbose Increase the verbosity of messages: 1 for normal output, 2 for more verbose output and 3 for debug
Help:
Discovers services information and credentials.
Modify Security Groups Command is an easy to use command that you can add to your DevOps to allow adding/Removing IPs or CIDRs to AWS security groups for all protocol and ports. The command is part of AWS PHP Commands.
Usage:
> php console.php aws:security-groups:modify -h
Usage:
aws:security-groups:modify [options]
Options:
-c, --cidr=CIDR CIDR ex: 64.18.0.0/20 [default: false]
-o, --operation=OPERATION Operation to perform, one of add or remove [default: "add"]
-e, --env[=ENV] Which security groups this should run on. One of prod, dev [default: "dev"]
-h, --help Display this help message
-q, --quiet Do not output any message
-V, --version Display this application version
--ansi Force ANSI output
--no-ansi Disable ANSI output
-n, --no-interaction Do not ask any interactive question
-v|vv|vvv, --verbose Increase the verbosity of messages: 1 for normal output, 2 for more verbose output and 3 for debug
Help:
Adds/removes CIDRs to security groups.
The script creates separate directory for every database and bz2 files for every table inside that database.
#!/bin/sh
#edit these
USER=""
PASSWORD=""
MYSQLDIR="/path/to/backupdir"
MYSQLDUMP="/usr/bin/mysqldump"
MYSQL="/usr/bin/mysql"
echo - Dumping DB structure "$MYSQLDIR"/all.bz2
$MYSQLDUMP --user=$USER --password=$PASSWORD -d --all-databases | bzip2 > "$MYSQLDIR"/all.bz2
echo - Dumping tables for each DB
databases=`$MYSQL --user=$USER --password=$PASSWORD -e "SHOW DATABASES;" | grep -Ev "(Database|information_schema)"`
for db in $databases; do
echo - Creating "$db" DB
mkdir $MYSQLDIR/$db
chmod -R 777 $MYSQLDIR/$db
for tb in `$MYSQL --user=$USER --password=$PASSWORD -N -B -e "use $db ;show tables"`
do
echo -- Creating table $tb
$MYSQLDUMP --opt --delayed-insert --insert-ignore --user=$USER --password=$PASSWORD $db $tb | bzip2 -c > $MYSQLDIR/$db/$tb.sql.bz2
done
echo
done
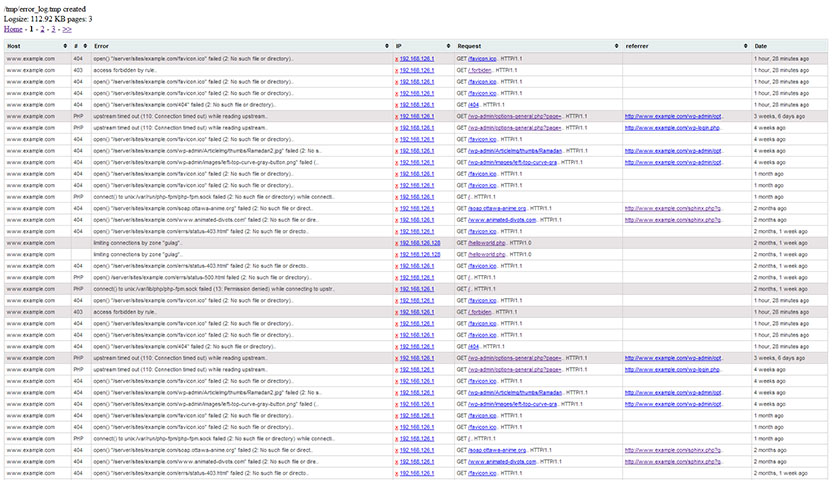 Nginx Error Log Reader is a php reader/parser/analyzer for Nginx error log file. the script is able to read error logs recursively then display them in a user friendly table. Script configuration includes the number of bytes to read per page and allow pagination through the error log . Additionally, table columns are sortable and full description of every error is displayed using MonnaTip.
Nginx Error Log Reader is a php reader/parser/analyzer for Nginx error log file. the script is able to read error logs recursively then display them in a user friendly table. Script configuration includes the number of bytes to read per page and allow pagination through the error log . Additionally, table columns are sortable and full description of every error is displayed using MonnaTip.
For banning Ips, please refer to this post Using iptables to block ips that spam or attack your server
– Make sure to check Nginx, PHP posts for information on Nginx and PHP setup and configuration.
Nginx offers two modules, HttpLimitReqModule and HttpLimitZoneModule, to limit simultaneous connections for the assigned session and the number of requests for a given session from one IP address. Basically these modules are built to protect the web server from possible DDos attacks; For example, this configuration limits remote clients to no more than 20 concurrently “open” connections per remote ip address:
http{
limit_conn_zone $binary_remote_addr zone=concurrent:10m;
limit_conn_log_level warn;
limit_conn concurrent 20;